When attempting to use SQL*Plus or other OCI based programs on either Red Hat Enterprise Linux or Oracle Enterprise Linux 5.0 or greater you receive errors such as the following.
[ejenkinson@aries ~]$ tnsping orcl tnsping: error while loading shared libraries: /u01/app/oracle/product/11.2.0/dbhome_1/lib/libclntsh.so.11.1: cannot restore segment prot after reloc: Permission denied [ejenkinson@aries ~]$ sqlplus /nolog sqlplus: error while loading shared libraries: /u01/app/oracle/product/11.2.0/dbhome_1/lib/libclntsh.so.11.1: cannot restore segment prot after reloc: Permission denied [ejenkinson@aries ~]$
If you look in the /var/log/audit/audit.log you will see something similar to the following.
type=AVC msg=audit(1272220424.619:34): avc: denied { execmod } for pid=2996 comm="sqlplus" path="/u01/app/oracle/product/11.2.0/dbhome_1/lib/libclntsh.so.11.1" dev=hda1 ino=8978342 scontext=user_u:system_r:unconfined_t:s0 tcontext=user_u:object_r:default_t:s0 tclass=file
type=SYSCALL msg=audit(1272220424.619:34): arch=c000003e syscall=10 success=no exit=-13 a0=2aeaa25db000 a1=228a000 a2=5 a3=2aeaa2677578 items=0 ppid=2971 pid=2996 auid=500 uid=500 gid=500 euid=500 suid=500 fsuid=500 egid=500 sgid=500 fsgid=500 tty=pts3 ses=1 comm="sqlplus" exe="/u01/app/oracle/product/11.2.0/dbhome_1/bin/sqlplus" subj=user_u:system_r:unconfined_t:s0 key=(null)
If you are running X-Windows you might also get a SELinux AVC denial pop up like the one below.
The reason for the denial is that SELinux is running in enforcing mode. You can verify by checking the status using sestatus.
[root@aries audit]# sestatus SELinux status: enabled SELinuxfs mount: /selinux Current mode: enforcing Mode from config file: enforcing Policy version: 21 Policy from config file: targeted [root@aries audit]#
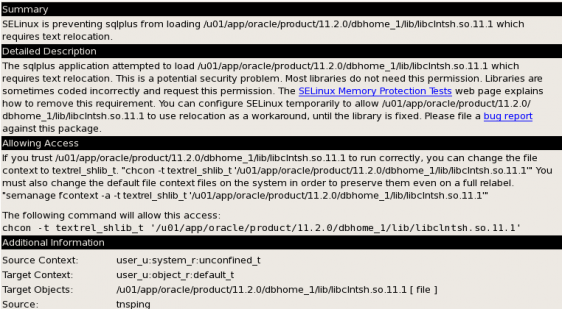
Clicking on the SELinux AVC denial pop up will bring up the SE Troubleshoot Browser that contains more detailed information. Below is screen shot of the information contained in the browser.
The descriptions details what the problem is, in this case the ORACLE_HOME/lib/libcIntsh.so.11.1 requires a text relocation. Why this is occurring has to do with an compiler version compatibility issue. This issue is documented in Oracle Support Note: 454196.1.
We could follow the advice for allowing access above for the library but the question we would have to ask is if there are possibly more libraries that might have this problem? Instead of guessing we could put SELinux in permissive mode. When SELinux is in permissive mode it still logs the denial messages but will not block the operation. Setting SELinux to permissive mode is also recommended by Oracle Support.
Note: This next section will detail the steps to change SELinux from enforcing to permissive. This is not a series of steps you should take lightly when working in a production environment.
You can set SELinux to permissive mode using the setenforce 0 command.
[root@aries ~]# getenforce Enforcing [root@aries ~]# setenforce 0 [root@aries ~]# getenforce Permissive [root@aries ~]#
The setenforce 0 command only sets permissive mode until the system is rebooted. After a reboot the SELinux will be back to enforcing. In order for permissive mode to persist through a reboot the /boot/grub/grub.conf file will need to be modified. Be sure to backup the file before editing. Below are the contents of the grub.conf file.
[root@aries etc]# ls -alh grub.conf
lrwxrwxrwx 1 root root 22 Apr 22 08:14 grub.conf -> ../boot/grub/grub.conf
[root@aries etc]# cat /etc/grub.conf
# grub.conf generated by anaconda
#
# Note that you do not have to rerun grub after making changes to this file
# NOTICE: You do not have a /boot partition. This means that
# all kernel and initrd paths are relative to /, eg.
# root (hd0,0)
# kernel /boot/vmlinuz-version ro root=/dev/hda1
# initrd /boot/initrd-version.img
#boot=/dev/hda
default=0
timeout=5
splashimage=(hd0,0)/boot/grub/splash.xpm.gz
hiddenmenu
title Enterprise Linux (2.6.18-194.el5)
root (hd0,0)
kernel /boot/vmlinuz-2.6.18-194.el5 ro root=LABEL=/ rhgb quiet
initrd /boot/initrd-2.6.18-194.el5.img
[root@aries etc]#
To change from enforcing to permissive we will add enforcing=0 to end of the line beginning with kernel.
kernel /boot/vmlinuz-2.6.18-194.el5 ro root=LABEL=/ rhgb quiet
becomes
kernel /boot/vmlinuz-2.6.18-194.el5 ro root=LABEL=/ rhgb quiet enforcing=0
After the changes have been made permissive mode will persist through reboots. Remember, even though SELinux is in permissive mode the denials are still occurring and being logged. If you are in X-Windows you will also see the SELinux AVC denial pop ups.

Thanks for the post. Really helped.
The workaround is well known. Have you come across a fix for running SELINUX in enforcing mode?
Hello Keith,
I have been able to run SELINUX in enforcing mode with Oracle 11gR2 patch set 11.2.0.3.0.
Eric Jenkinson
Very useful.
Thanks a lot!!!
Thanks, It is very helpful.
I faced this problem log back but was able to resolve it.
today i faced it again and did’nt remember the steps to resolve.
Thanks for quick help. i could solve it in a min 🙂
-Muneer
thank you very much, it helped me a lot……..
After knowing through this post that the error is because of SE Linux being in enforcing mode instead of permissive, I entered the Linux setup as:
> setup
In the console mode/GUI -> Firewall Configuration -> Selected permissive mode(instead of enforcing mode).
I suppose this would be an easier way to change SELinux mode other than the commands. Hope this will solve current issues.
Thanks a lot… very useful. 🙂
thank god this is what i need…
but y dont you explain each n every step in detail why we get this type of errors.
Yes really a good link…
THANK YOU. IT REALLY HELPED.